Page 63 - 108
P. 63
the completion of the maintenance activity.
The rapid evolution of the Finally, an intrusion detection system (IDS) can be
electrical grid due to the easily integrated into an SDN network. SDN ap-
“growing dispatch of renewable pliances can be instructed to forward undesired
packets (if not all the traffi c) to the IDS server, thus
energy resources is driving potentially making dedicated sensors redundant.
the energy sector to demand a
deterministic, secure, reliable,
and controllable infrastructure Conclusion
that can be deployed and With all previous considerations, it is clear why
SDN has gained signifi cant traction in the industry
managed using modern tools over the past few years.
and technology Many commercial switches support the OpenFlow
API, and programmers have used these platforms
to create many different applications, such as
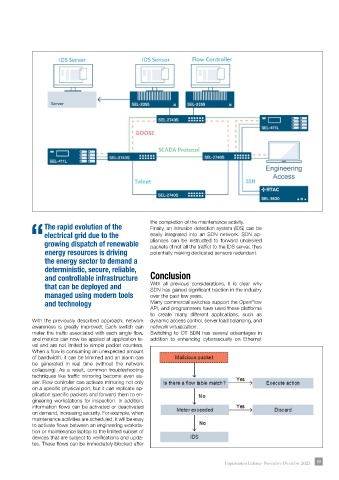
With the previously described approach, network dynamic access control, server load balancing, and
awareness is greatly improved. Each switch can network virtualization.
meter the traffi c associated with each single fl ow, Switching to OT SDN has several advantages in
and metrics can now be applied at application le- addition to enhancing cybersecurity on Ethernet
vel and are not limited to simple packet counters.
When a fl ow is consuming an unexpected amount
of bandwidth, it can be trimmed and an alarm can
be generated in real time (without the network
collapsing). As a result, common troubleshooting
techniques like traffi c mirroring become even ea-
sier. Flow controller can activate mirroring not only
on a specifi c physical port, but it can replicate ap-
plication specifi c packets and forward them to en-
gineering workstations for inspection. In addition,
information fl ows can be activated or deactivated
on demand, increasing security. For example, when
maintenance activities are scheduled, it will be easy
to activate fl ows between an engineering worksta-
tion or maintenance laptop to the limited subset of
devices that are subject to verifi cations and upda-
tes. These fl ows can be immediately blocked after
Impiantistica Italiana - Novembre-Dicembre 2023 59