Page 23 - 78
P. 23
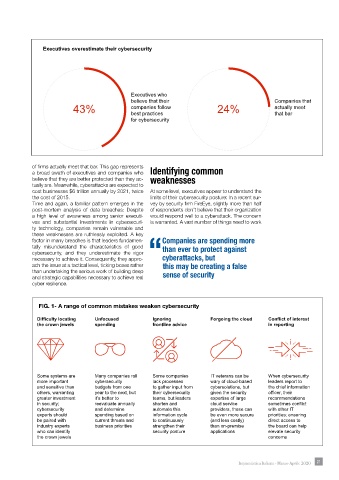
Executives overestimate their cybersecurity
Executives who
believe that their Companies that
43% companies follow 24% actually meet
that bar
best practices
for cybersecurity
of firms actually meet that bar. This gap represents
a broad swath of executives and companies who Identifying common
believe that they are better protected than they ac- weaknesses
tually are. Meanwhile, cyberattacks are expected to
cost businesses $6 trillion annually by 2021, twice At some level, executives appear to understand the
the cost of 2015. limits of their cybersecurity posture: In a recent sur-
Time and again, a familiar pattern emerges in the vey by security firm FireEye, slightly more than half
post-mortem analysis of data breaches: Despite of respondents don’t believe that their organization
a high level of awareness among senior executi- would respond well to a cyberattack. The concern
ves and substantial investments in cybersecuri- is warranted. A vast number of things need to work
ty technology, companies remain vulnerable and
these weaknesses are ruthlessly exploited. A key
factor in many breaches is that leaders fundamen- Companies are spending more
tally misunderstand the characteristics of good than ever to protect against
cybersecurity, and they underestimate the rigor
necessary to achieve it. Consequently, they appro-“cyberattacks, but
ach the issue at a tactical level, ticking boxes rather this may be creating a false
than undertaking the serious work of building deep
and strategic capabilities necessary to achieve real sense of security
cyber resilience.
FIG. 1- A range of common mistakes weaken cybersecurity
Difficulty locating Unfocused Ignoring Forgoing the cloud Conflict of interest
the crown jewels spending frontline advice in reporting
Some systems are Many companies roll Some companies IT veterans can be When cybersecurity
more important cybersecurity lack processes wary of cloud-based leaders report to
and sensitive than budgets from one to gather input from cybersolutions, but the chief information
others, warranting year to the next, but their cybersecurity given the security officer, their
greater investment it’s better to teams, but leaders expertise of large recommendations
in security; reevaluate annually shorten and cloud service sometimes conflict
cybersecurity and determine automate this providers, these can with other IT
experts should spending based on information cycle be even more secure priorities; ensuring
be paired with current threats and to continuously (and less costly) direct access to
industry experts business priorities strengthen their than on-premise the board can help
who can identify security posture applications elevate security
the crown jewels concerns
Impiantistica Italiana - Marzo-Aprile 2020 21
Source: Bain & Company